
Bit of a boring write-up, but here we go. Taxi app Gett had a content injection flaw in its search function. By searching for an HTML string, it was possible for an attacker to add links or images to a page. It was really hard to contact them - but the threat of media attention […]
Continue reading →

Recently, one of the accounts I follow on Twitter was hijacked. It was turned into a PS5 giveaway scam. The people who hijacked the account changed the name, avatar, and deleted all the previous Tweets. Here's how I found who the original owner was, and managed to contact them. A Twitter account has a screen […]
Continue reading →

One of the problems with OEmbeds of Tweets is that they're heavy. Lots of JavaScript, tracking cookies, and other detritus. See this excellent post by Matt Hobbs looking at how to make your website faster by removing Twitter embeds and replacing them with images. Here's my attempt to turn a Tweet into a semantic SVG! […]
Continue reading →

I have built the most inconvenient way of playing music! It is lo-fi awfulness and cyberpunk grungy. Thanks! I hate it! Ingredients Raspberry Pi USB floppy drive Audio Cable / Headphones USB Battery WHY?!?! As I discussed yesterday, it's possible to fit half an hour of speech on a single floppy disk. The best band […]
Continue reading →

Short domains are useful for security testing. If you only have a limited number of characters, you need to be able to reference code on a remote server in as few characters as possible. A few years ago, I tried to find a Minimum Viable XSS. The conclusion that I (and others) came to is […]
Continue reading →

I write book reviews on my blog. I also want to syndicate them to Goodreads. Sadly, Goodreads doesn't natively read the Schema.org markup I so carefully craft. So here's the scrap of code I use to syndicate my reviews. Goodreads API Keys Get your Keys from https://www.goodreads.com/api/keys You will also need to get OAuth tokens […]
Continue reading →

I go to lots of hack days and hackathons. Some are big corporate affairs, some are boutique community events. They all have one thing in common - Geeks suck at giving demos. You have 3 minutes to convince the judges - or your peers - that you've built something brilliant. How do you do that? […]
Continue reading →

Six years ago, I developed Android apps (APKs) which I emailed to myself. When I try to download them from Gmail today, I get this rather annoying error. Anti-virus warning – 1 attachment contains a virus or blocked file. Downloading this attachment is disabled. Google, in its efforts to protect me from myself, have retroactively […]
Continue reading →

There's a new bug bounty provider in town! The Belgian company Intigriti. This is a quick write-up of how I found a trivial bug in their own system. The EU has announced that it is providing funding for bug bounties on critical open source projects. They've split the programme between HackerOne and Intigriti. I signed […]
Continue reading →
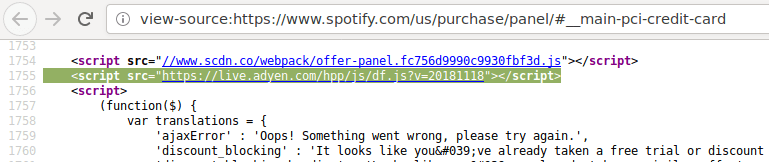
A few months ago, British Airways' customers had their credit card details stolen. How was this possible? The best guess goes something like this: BA had 3rd party JS on its payment page <script src="https://example.com/whatever.js"></script> The 3rd party's site was hacked, and the JS was changed. BA's customers ran the script, which then harvested their […]
Continue reading →
