What is a public key and how does it work?
In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is provided by a trusted, designated authority and made available to everyone through a publicly accessible repository or directory.
What is public key encryption?
In encryption, two main types of cryptographic algorithms are used. These are symmetric and asymmetric. Symmetric key algorithms work by using a single key to encrypt and decrypt information. In contrast, asymmetric cryptography uses two keys: a public key to encrypt messages and a private key to decode them.
Public keys are created using an asymmetric algorithm, which pairs the public key with an associated private key. The most common algorithms used to generate public keys are Rivest-Shamir-Adleman, elliptic curve cryptography and Digital Signature Algorithm.
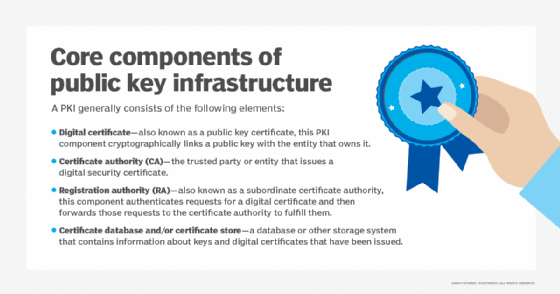
Public keys are available from a certificate authority, which issues digital certificates that prove the owner's identity and contain the owner's public key.
How public key encryption works
A cryptographic key is a mathematical algorithm implemented in software or hardware and used to encrypt or decrypt data. It is a string of bits that are combined with the data to create ciphertext. The cryptographic key can also be used to unencrypt data back to plaintext.
The same key can be used to both encrypt and decrypt the message, or different keys can be used for each of these steps in the encryption process. With the latter, the keys are known as public and private keys.
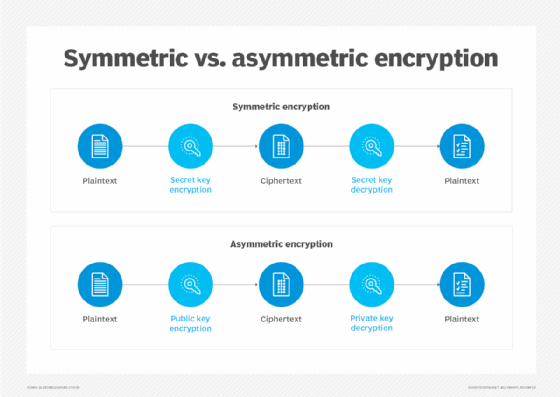
The process for sending and receiving data via asymmetric cryptography typically consists of five steps:
- Key generation. Each individual generates a public and private key.
- Key exchange. The sender and recipient exchange public keys.
- Encryption. The sender's data is encrypted using the recipient's public key.
- Sending encrypted data. The encrypted data is sent to the recipient.
- Decryption. The recipient decrypts the message using their own private key.
Importance of public keys
Both public and private keys are essential elements in public keys -- also known as asymmetric cryptography. A public key is used to encrypt a message and a private key, held only by the recipient, is used to decrypt the message. Encryption helps to protect sensitive or confidential information, especially when it travels from a sender to a recipient.
Public keys are also needed to create digital signatures and to check the legitimacy of these signatures during the transmission of secure digital information. While the private key creates the signature, the public key validates it, thus authenticating the sender's identity. The public key also confirms that the message (that was signed with the digital signature) is not tampered with during transmission and thus ensures its integrity and confidentiality.
Public key applications
The main applications of public key technology are:

Encryption
One of the main uses of a public key is to encrypt messages prior to sending. Since the public and private keys are mathematically connected, they are used together to encrypt and decrypt information. If anyone other than the owner of the private key tries to decrypt the information using the public key, the information will be unreadable.
The use of two different keys makes it harder for unauthorized or malicious parties to eavesdrop on a digital transaction or to steal or compromise the message.
Digital signatures
Public key encryption is also used to create digital signatures. The digital signatures are generated via the following steps:
- The sender identifies the file to be digitally signed.
- The document application on the sender's computer calculates a unique hash value for the contents of that file.
- The sender's private key is used to encrypt the hash value, creating the digital signature.
- The original file and the digital signature are sent together to the recipient.
- The recipient uses the sender's public key to decrypt the digital signature's hash.
- The recipient's computer calculates the hash of the original file and compares it with the decrypted hash. If the two hashes match, the signature is verified. If the hashes don't match, that's evidence that the document has been altered or that the signature isn't valid.

Secure Socket Layer and Transport Layer Security connections
SSL/TLS use public key encryption to create a secure connection between the server and client. This encryption method enables the use of HTTPS. The public key is contained in the SSL/TLS certificate, which is publicly shared. The private key however is installed on the website's origin server.
The communication session is first established (known as a handshake) using asymmetric encryption. This establishes the identities of both parties and facilitates the exchange of a shared session key that enables a symmetric cipher. A key exchange algorithm uses the public-private key pair to agree upon the session keys. These keys are then used for symmetric encryption. For each session, new session keys are generated and agreed upon to prevent unauthorized parties from decrypting the message using older session keys.
Cryptocurrencies
Public keys and digital signatures are also used for cryptocurrency transactions. In fact, in such transactions, public keys are used as digital signatures to create crypto public addresses, prove a user's ownership of the private key, and authorize the user to make transactions (buy, sell, hold, etc.) from their crypto account.
The public key is a hashed version of the private key, making it useful to do the following:
- Prove that the digital signature came from the private key.
- Verify and validate transactions.
How does a public key differ from a private key?
In asymmetric cryptography, a public key is accompanied by a corresponding private key, which is known only to its owner. Simply put, a public key locks up data from unauthorized use, while a private key is used to unlock it.
A public key can be given to any person with whom an individual wants to communicate and is available for anyone to use, whereas a private key belongs only to the individual it was created for. The public key is typically stored on a public key infrastructure server and is used to encrypt data before it is sent over the internet.
Symmetric encryption uses a shared key, making it faster and more efficient than asymmetric encryption -- so it makes sense to use it for a lot of digital communications. However, the shared key can be stolen, increasing the potential for transactional compromise and data theft. For this reason, it is unsuitable for transactions where high security is of prime importance, such as crypto, banking or e-commerce.
Public key risks
While public key encryption is more secure than symmetric encryption, there are a few risks to consider, including the following:
- Low-quality key. A poorly crafted asymmetric key algorithm -- one that's too short in length, for example -- is a security risk. To ensure secure digital transactions and to avoid security events like brute force attacks, public keys must be as long and as random as possible.
- Key mismanagement. Public keys must be properly distributed and rotated to minimize theft and prevent cyberattacks. In applications like SSL/TLS, new session keys must be generated for each new communication session to prevent reuse by threat actors.
- Lost private key. If the private key is lost or misplaced, the authorized recipient might not be able to access the data.
- Man-in-the-middle attacks. Public key encryption can be a target for MitM attacks. The two main ways of trusting the identity of a website are the site's security certificate and its public key encryption. If either of these is compromised, a malicious party can insert itself into the connection between a user and a website and then capture any information sent between the two. This can be particularly dangerous if the information is sensitive or private, such as credit card numbers or login passwords.
The above risks can be mitigated by using the strongest encryption algorithms like RSA, Advanced Encryption Standard (AES) or Blowfish. It's also important to generate keys of appropriate length and randomness, and to periodically rotate keys. Users can also avoid many security issues by verifying the authenticity of digital certificates before trusting any public keys.
The origin of public key encryption
In 1976, Whitfield Diffie, Martin Hellman and Ralph Merkle published a paper titled New Directions in Cryptography in which they introduced the idea of public key cryptography and described the first known functional distributed cryptographic protocol. That said, other individuals and agencies have also claimed to have developed public key cryptography, such as the British Communications Electronics Security Group and the USA's National Security Agency (NSA). However, it was mainly Diffie's and Hellman's work that resulted in what is known as the Diffie-Helman key exchange: a public key protocol in which two keys are generated, two parties jointly establish a shared secret key, and the key is then used to encrypt and secure communications between those parties.
Since the early days of public key cryptography, various public key encryption algorithms have been developed. These algorithms are used in a wide range of applications in finance, e-business, and e-commerce to keep data secure by using two mathematically related keys.
Learn everything you need to know about data security in general in this ultimate guide to the topic.



